Cryptowall: New virus high risk to Business – Remove instructions Step By Step completely
Posted on: Wednesday November 26 in Computer Maintenance, On-Site, Virus Removal tagged by RonenA new threat virus called Cryptowall with high risk to business, is your business secure?
Using anti-virus protection won’t provide you the protection you need against the new Cryptowall encryption malware there is always a risk getting this virus.
If one of your computers infected with Cryptowall encryption we will advise you to read our step by step instructions how to remove it completely and Safely.
The virus will encrypts all your pdf, images, word, power point, excel and data on your network, although there is a way to remove the first version of this Cryptolocker malware it seem that version 2.0 called Cryptowall will be harder to deal with.
About Cryptolocker malware:
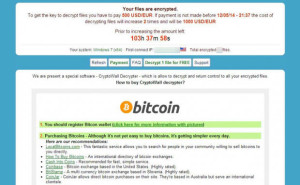
Cryptolocker is a Trojan horse that encrypts files on the compromised computer. Then asking the user to pay to have the files decrypted.
Cryptolocker known as ransom-malware (ransomware) after infecting all your files you will receive offer to decrypts in exchange for paying ransom money.
After infecting one computer it may infect your all network
How do we get Cryptolocker malware or any virus and Malware?
Typically arrives through spam emails, exploit kits hosted through malicious ads or compromised sites, or other malware.
Viruses infecting computers are as common, sooner or later, it’s just going to happen.
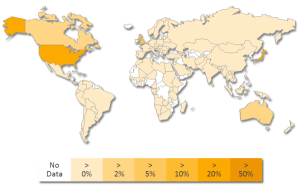
Geographical distribution
Symantec has observed the following geographic distribution of this threat:
How does it infect a computer?
How does it infect a computer and your network?
Once your computer infected, it gets a hold of your computer, establishing network connection to random servers, then start to upload your computer connection info, including your location, and system information.
Next, the remote server will generate a random encryption of 2048-bit RSA key pair that’s associated with your computer. Copy the public key to the computer and begins the process of copying each file on its pre-determined list of supported file extensions. As a copy is created, it’s encrypted using the public key, and the original file is deleted from the hard drive. Until all the files matching the supported file types have been copied and encrypted.
My option once my computer is infected?
- Paying ransom
- Restore to factory default your computer and recover from backup
- Removing the Trojan and recovering data with our step by step instructions
How To Avoid getting the virus:
do not open any email that you may not recognize, do not download PDF / Images /Document / Zip file from non-expected email, once you browse the internet and it start downloading images / file without you requesting and knowing what it is – Cancel it / Close the internet Browser.
If you receive a message on your desktop – DO NOT CLOSE IT, save all the files you are working and force shut down of the computer.
Step by step instructions how to remove Cryptowall Trojan:
Before starting we will advise you to write our contact info BA Consulting the best I.T. Consulting in Greater Toronto Area (647) 401-8646 we will be happy to assist you to remove this virus and for any Computer, IT services and consulting.
* we strongly advise you to use our services – removing by yourself or any none professional experience it is your
risk only, we have tested our instruction and removed in our lab.
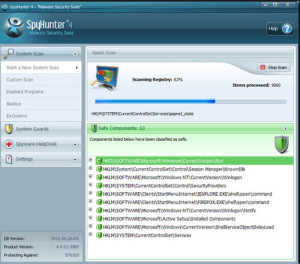
- Download Malwarebytes, CCleaner , RogueKiller and install with Admin rights
- Turn off your computer, and restart to safe mode (by pressing F8 after turning on the computer before windows loaded, you will get black screen with option to choose SAFE MODE. (use the keyboard arrow to navigate)
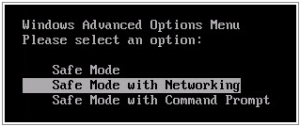
- Once you access your computer press windows + R
 If you are having a problem accessing your computer ( do not know your local password in safe mode) Contact US
If you are having a problem accessing your computer ( do not know your local password in safe mode) Contact US
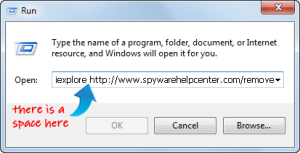
4. iexplore https://spywarehelpcenter.com/remove
5. Install the software and run it
6. Now you will need to remove / uninstall CryptoWall Decrypter
If using win XP:
1. Open the Start menu, click Control Panel and double-click Add or Remove Programs.
2. Select the undesirable application and click Remove.
If you use Windows Vista/Windows 7:
1. Click Start (left of the Task Bar) and select Control Panel.
2. Go to Uninstall a program and right-click the application you wish to remove.
3. Select Uninstall.
If you use Windows 8:
1. Right-click on the Metro UI start screen and select All apps.
2. Open Control Panel and click Uninstall a program.
3. Right-click the application you want to remove and select Uninstall.
7. run all the software
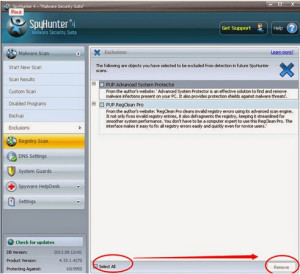
Second, clean up residual junk files and invalid registry entries from computer
%temp%\ HowDecrypt.txt.exe C:\Program Files\ HowDecrypt.gif. HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\msmpeng.exe HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\msseces.exe





 BA Consulting has been our “go to” IT company for the last 4 years.
BA Consulting has been our “go to” IT company for the last 4 years.
Comments are closed.